Synopsis
Personal identity thefts and cyber attacks have kept businesses at stake. Recent years have witnessed soaring rates of cybersecurity incidents. Personal information of distributors, customers, and stakeholders is often a desirable target for cybercriminals.
Cyberattacks are becoming more targeted and sophisticated. Irrespective of having a security framework, organizations still loom in the unfortunate cycle of events resulting in wavering customer trust. Maintaining high-security standards thus becomes imperative for MLM companies to win customer confidence and operate smoothly in the evolving threat landscape.
Problem
An MLM health and wellness business needed to revamp their defense framework due to the concurrent issues they were facing in the complex business environment. Despite their numerous efforts to safeguard organizational data, cyber incidents kept occurring putting the business at the verge of legal scrutiny.
Persistent cyber incidents and legal complications accelerated the need for a comprehensive security infrastructure.
Customer attrition rates peaked with increase in data breach concerns. Probably in the fear of losing their personal and financial information, customer sign ups and distributor registration rates declined. A transparent and concerted effort was highly in demand in order to communicate the brand’s commitment to customer data protection.
Solution
Addressing emerging threats and broader security issues recommended governance, risk, and compliance activities to reduce associated risks and ensure overall security. Implementation of a robust security framework also had to ensure that the efforts are consistent with the overall cybersecurity strategy of the organization.
Epixel MLM Software ran a comprehensive risk assessment factoring in both internal and external risks to the organization. Through rigorous brainstorming and extensive documentation, the team gathered information to assess the probability and impact of identified risks. Taking into consideration the varying levels of effectiveness and feasibility, we created a tailored customer-inclusive security management solution that assisted in risk mitigation and controls.
Role-based access controls
User roles were determined based on individual responsibilities within the organization and everyone was given specific set of rights to access the organization’s database. Distributors, business admins, employees, and stakeholders each were defined a distinct role in the system with access privileges given based on the same.
Distributors were given access to managing daily tasks and that of their downlines, overseeing and generating sales, commission, and team performance reports.
Highly confidential and sensitive information were accessible only to the admins. Privileges to customize and configure the system rests solely on the admin highlighting the pivotal role they play in maintaining the integrity and security of data across business processes.
Granting and revoking permissions were automated to ensure that the access control remains efficient, accurate, and aligned with the dynamic nature of the MLM business.
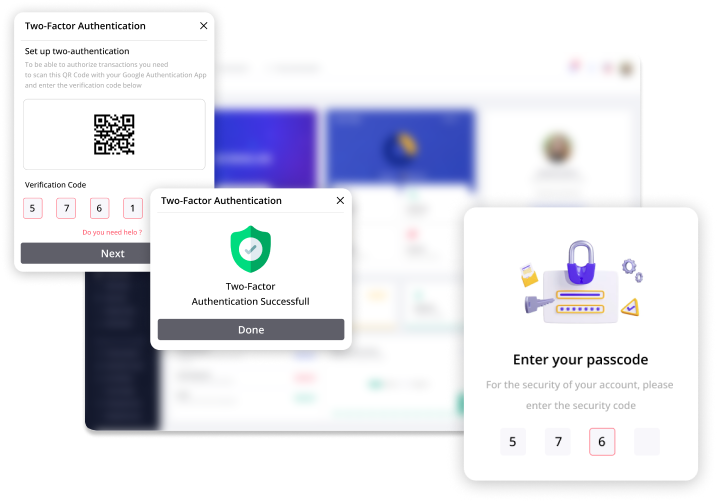
Secure authentication mechanisms

Robust authentication mechanisms like Multi-Factor Authentication (MFA), Single Sign-On (SSO), and certificate-based authentication were integrated to ensure secure access to organizational information.
MFA employed two or more verification steps to grant users access to the database. With Single Sign-On feature users need to log in only once gaining access to multiple connected systems without entering the credentials again. This simplified user efforts and the number of passwords used, still reinforcing the needed security for the system. Certificate-based authentication was assigned to high-priority transactions.
Risk-based authentication analyzes each login activity and adds additional authentication steps to add an extra layer of security. Time-based OTPs (One-Time Passwords) generate passwords with time limit to reinforce security during transactions.
With a multi-layered approach, various security measures were implemented at different levels to create a comprehensive defense mechanism.
Advanced encryption protocols
All the organizational communication channels and transactions were integrated with end-to-end encryption to ensure the safety of data in transit. All MLM transactions were decentralized with blockchain technology enhancing the integrity and security of the transactions.
Password management
Maintaining the security of user credentials required a reliable password management system. We helped the organization implement complex password policies with specific password generation requirements enhancing overall password complexity. The automated password management system prompted users to regularly update their password mitigating the potential impact of compromised credentials overtime.
Secure payment integration
Sensitive financial data was secured within a system that aligned with Payment Card Industry Data Security Standard (PCI DSS). All payment-related functionalities were integrated with advanced authentication mechanisms like 3D secure protocols, Time-based One-Time Passwords (TOTPs), and Multi-Factor Authentication (MFA), to protect against unauthorized access to financial data thus improving the credibility of transactions.
Compliance alignment
As a business operating in the global marketplace, aligning with global data privacy laws such as GDPR, CCPA, HIPAA, PIPEDA, SOX, etc is crucial. An automated compliance system maintains that the brand comply with these international standards to ensure the privacy and security of customer data.
Customer-inclusive security strategy
With a view to communicating the brand’s commitment to safeguarding customer data, a customer-inclusive security strategy was drafted. It actively involves customers in ensuring the security of their data through privacy controls that allowed them to customize their security settings. Customers were clearly notified on how their data is handled, stored, and protected. They were also promptly informed on new security updates and enhancements.
Regular security patching and audits
Besides maintaining a strong security posture, the ever-changing nature of the business demanded constant monitoring of the system. Regular security patches and updates ensured that critical vulnerabilities were addressed promptly. Security audits were conducted regularly to identify vulnerabilities, weaknesses, areas, and processes for improvement. This proactive strategy helped mitigate and adapt to emerging threats maintaining a secure environment for organizational data and systems.
Data backup and recovery
Regular backup of essential databases, user profiles, and transaction history ensured consistency in the data flow process. The backed up data was stored both on-premises and in the cloud, making it easier to recover data in the event of unexpected security incidents.
Challenges We Faced
Identifying, analyzing, and evaluating the potential risks that may hamper the integrity and efficiency of the organization demanded a strategic approach. We had to ensure that the security measures we implement would also align with the organizational policies. Hence, we had to extend the scope and define the boundaries carefully.
Identifying critical data assets from an enormous database demanded rigorous attention to detail. Given the complexity of potential risks and the amount of data involved, we had to consider both qualitative and quantitative methods. Operating in the direct selling sector demanded a security architecture that also aligns with the legal and regulatory guidelines.
Continuous monitoring of changing business environment was the most challenging responsibility to undertake. A dedicated support team regularly reviews and updates the system to ensure that it remains resilient to changing circumstances and emerging threats.
Expected Results
Decrease in cyber incidents
17%
Improved data quality
21%
Transaction success rate
25%
Reduced customer attrition rates
19%
Increase in distributor enrolment rate
18%
Reduced data breach incidents
28%
Security audit compliance
95%
Encryption effectiveness
100%
Improved access control monitoring
100%
Reduced incident response time
100%
User authentication success rate
100%
Improved security patching compliance
98%
Decrease in cyber incidents
17%
Improved data quality
21%
Transaction success rate
25%
Reduced customer attrition rates
19%
Increase in distributor enrolment rate
18%
Reduced data breach incidents
28%
Security audit compliance
95%
Encryption effectiveness
100%
Improved access control monitoring
100%
Reduced incident response time
100%
User authentication success rate
100%
Improved security patching compliance
98%
Build a customer-centric security system to safeguard your network marketing business and your customer trust
Free Demo
